GCP Vertex AI
Vertesia uses Workload Identity Federation to access GCP services, and act as an OIDC Identity Provider for GCP.
In practice this means that Vertesia present a Vertesia-generated, cryptographically-signed token (JWT), that is verified by GCP Secure Token Service, and then STS issues in exchange a short lived access token that assign the role and permissions defined in IAM.
Thanks to this approach, you can set fine grained permissions on any environment or account in Vertesia.
In addition to this documentation page, a helper script which automates all the configuration steps is available here
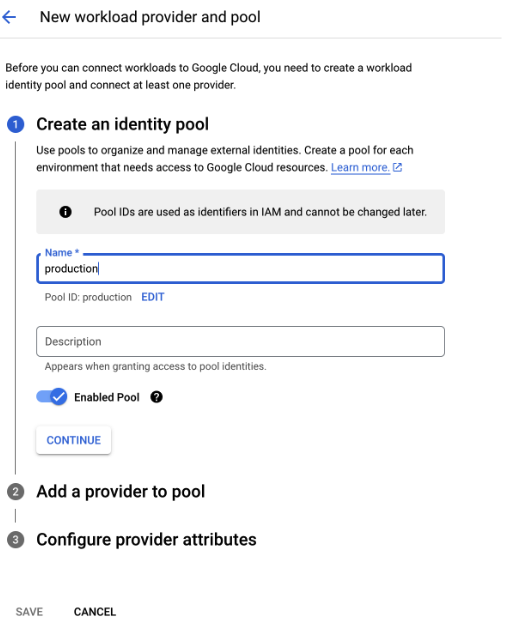
Create an Identity Pool
If you want to add a provider to an existing pool, skip this step and go directly to the next section
- Open the Google Cloud Console
- Go to Workload Identity Pools
- Create a new pool (you can use any name)
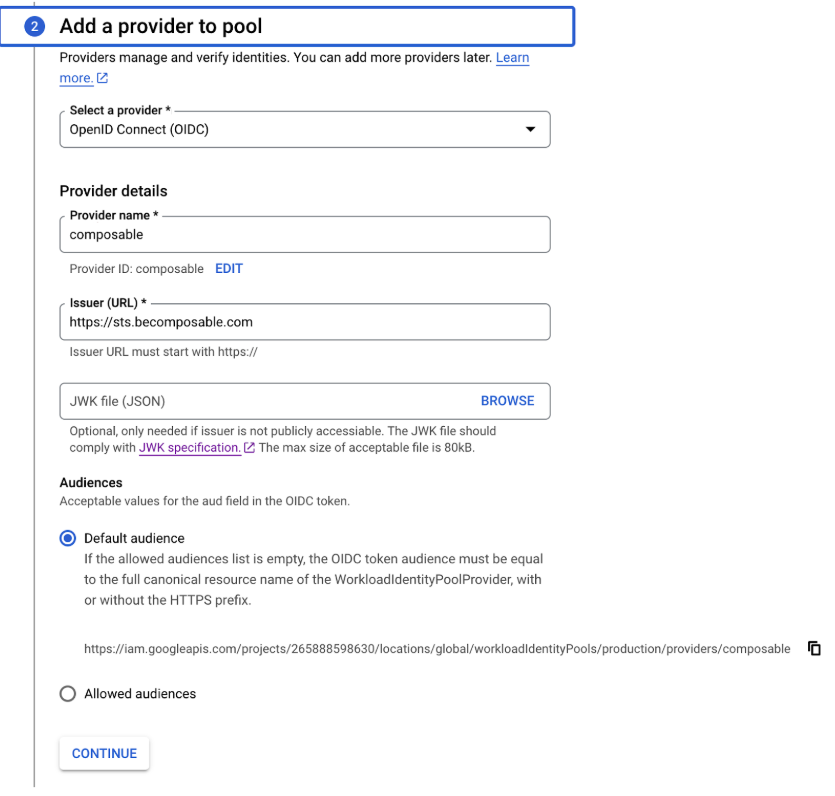
Configure a Provider
- Provider: OpenID Connect (OIDC)
- Name: vertesia
- Issuer URL: https://sts.becomposable.com
- Copy the
default audience url
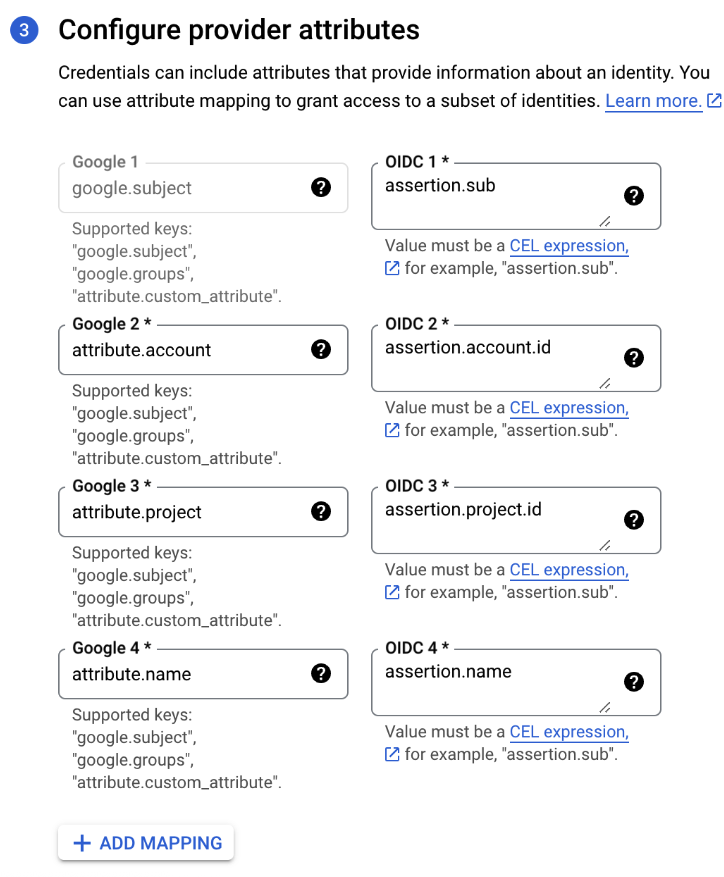
- Configure the provider attributes to map Vertesia’s token attributes to the Google’s principal attributes:
| Google Attributes | OIDC attributes |
|---|---|
| google.subject | assertion.sub |
| attribute.account | assertion.account.id |
| attribute.project | assertion.project.id |
| attribute.name | assertion.name |
On the pool details page, after the creation, copy the IAM principal value:
principal://iam.googleapis.com/projects/PROJECT_ID/locations/global/workloadIdentityPools/POOL_NAME/subject/SUBJECT_ATTRIBUTE_VALUE
Grant Permissions
You now need to give permissions to your Vertesia identity pool access to VertexAI.
- Go to IAM
- Click on Grant Access to set a role on a principal
- Set the principal to the URL you noted above, adding your Vertesia account ID:
principal://iam.googleapis.com/projects/PROJECT_ID/locations/global/workloadIdentityPools/POOL_NAME/attribute.account/ORGANIZATION_ID- To get the value for ORGANIZATION_ID, Open Vertesia Studio
- You can display your Organization ID by clicking on the user info icon in the top right corner of the Studio UI
- Select Vertex AI User and Service Account Token Creator as a role, or a custom role if you have created one
Other principal formats can be use to make access more restrictive:
- Only a specific execution environment:
principal://iam.googleapis.com/projects/PROJECT_ID/locations/global/workloadIdentityPools/POOL_NAME/subject/env:ORGANIZATION_ID:ENVIRONMENT_ID - Only request coming from a specific project:
principalSet://iam.googleapis.com/projects/PROJECT_ID/locations/global/workloadIdentityPools/POOL_NAME/attribute.project/PROJECT_ID
Configure a new Vertesia Execution Environment
In Vertesia, go to Environments, you can now add a new environment for the provider Google Vertex AI, and set the following:
- API Key: set
the default audience URLthat you have noted in Configure a Provider - Endpoint: set it to
REGION_NAME:GOOGLE_PROJECT_NAME, for exampleus-central1:myvertesiaproject
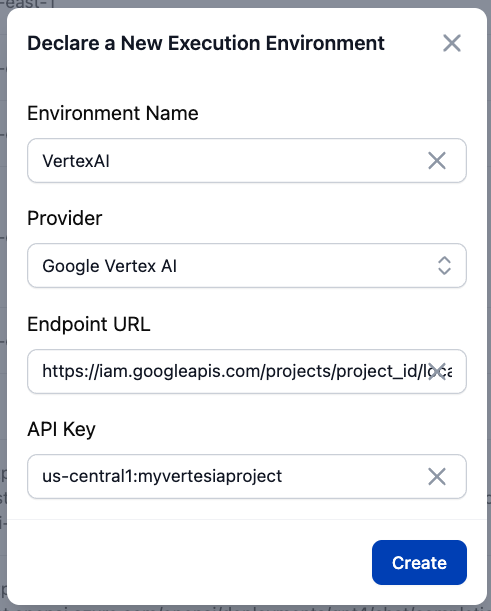
Save, refresh the page. Models should now list, and you can enable models in your environment.
